Now you are staring at your screen looking for culprits after downloading the logged pcap files. You are considered performing offline pcap analysis as you don't make contacts to the network while doing it but I'm sured most of you will need internet connection to acquire necessary data sometimes so you will still leave your internet connection on.
Most people do not know that they are actually generating network traffic when they performing analysis on pcap files, and they are telling you they are doing it offline. But this is totally not right. Take a look at the screenshot below.
Most people do not know that they are actually generating network traffic when they performing analysis on pcap files, and they are telling you they are doing it offline. But this is totally not right. Take a look at the screenshot below.
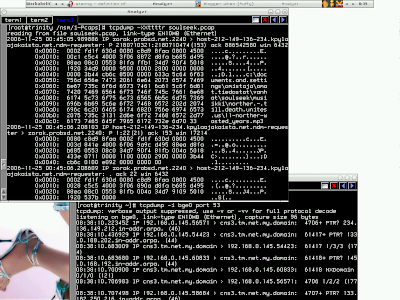
I'm running two virtual terminal, the first shows I'm running -
shell>tcpdump -XXttttr soulseek.pcap
At the same time I monitor my network interface in second virtual terminal -
shell>tcpdump -i bge0 port 53
If you look at the second one, apparently there are dns traffics ongoing. Yes, I'm using tcpdump, but most of network analysis tools will try to resolve the host address or port when possible if you are not telling them not to do it. Now you still consider performing offline analysis, I bet no. To actualy do it, you will have to run tcpdump with -n option, by doing that you don't convert host address and port number to name anymore.
shell>tcpdump -XXttttnr soulseek.pcap
Now you will see no network traffics generated, this is the real offline pcap analysis. And guess what, you gain extra speeds when analyzing large pcap file since you don't try to resolve the host addresses or ports(refer /etc/services file) anymore.
Remember this is not only applied to tcpdump but many other network analysis tools(argus, wireshark and so forth).
Enjoy (;])
Remember this is not only applied to tcpdump but many other network analysis tools(argus, wireshark and so forth).
Enjoy (;])
P/S: On linux, specify -n alone will prevent from doing dns lookup, however it will still tries to convert the port number to name, you will have to run -nn to avoid resolving anything.
3 comments:
A good tool for analyzing PCAP files offline in Linux is NTop. If you rather want to run Windows I would recommend NetworkMiner.
You can also use PCAP2XML tool for advanced PCAP analysis.
Have a look on this blog and tool:
Blog: - http://hackoftheday.securitytube.net/2015/03/pcap2xmlsqlite-convert-80211-packets-to.html
Tool: - http://www.pentesteracademy.com/course?id=17
You can also use PCAP2XML for PCAP analysis:
Have a look:
Tool: - http://bit.ly/1DxcncQ
Blog: - http://bit.ly/1DxciWG
Post a Comment