This looks like interesting dual ports network adapter with bypass function, more information ->
http://www.portwell.com/products/detail.asp?CUSTCHAR1=ABN-192
If you know where can get this in Malaysia, please do let me know.
Tuesday, December 23, 2008
Saturday, December 20, 2008
NIDS: Administration, Management & Provisioning
We often find many resources that discuss about NIDS technologies, and how can you setup one, however things that are really missed out there(even in the internet) should be the following.
If you are managing tons of Network Intrusion Detection systems(NIDS), for tons I mean more than 50, I would like to hear from you about -
1. What tools do you use to manage all the NIDS, and why you choose them over others?
- For example ssh, however I would like to know more about tools you use to manage massive NIDS instead of one, and the reason you choose it.
2. How do you perform efficient administration securely? For examples,
- System changes/updates
- NIDS tools' changes/updates
- NIDS rules' changes/updates
- NIDS Configuration files' changes/updates
- NIDS Policies' changes/updates
3. Which method you like to use in order to manage them, and why? For example,
- Server pushes rules update to all the sensors(Push)
- Sensors pull the rules update from server(Pull)
3. NIDS health monitoring and self-healing
- I'm talking about something like this, if the system is in incosistent state, operators will be notified. If certain process die, it should recover by itself.
I consider NIDS as critical system and it should be managed wisely to prevent misconfiguration, downtime and so forth. Therefore we should have solid answers for the questions above if we are going for massive NIDS implementation and deployment.
Any in sight or valuable thoughts to share are welcomed!
Peace ;]
If you are managing tons of Network Intrusion Detection systems(NIDS), for tons I mean more than 50, I would like to hear from you about -
1. What tools do you use to manage all the NIDS, and why you choose them over others?
- For example ssh, however I would like to know more about tools you use to manage massive NIDS instead of one, and the reason you choose it.
2. How do you perform efficient administration securely? For examples,
- System changes/updates
- NIDS tools' changes/updates
- NIDS rules' changes/updates
- NIDS Configuration files' changes/updates
- NIDS Policies' changes/updates
3. Which method you like to use in order to manage them, and why? For example,
- Server pushes rules update to all the sensors(Push)
- Sensors pull the rules update from server(Pull)
3. NIDS health monitoring and self-healing
- I'm talking about something like this, if the system is in incosistent state, operators will be notified. If certain process die, it should recover by itself.
I consider NIDS as critical system and it should be managed wisely to prevent misconfiguration, downtime and so forth. Therefore we should have solid answers for the questions above if we are going for massive NIDS implementation and deployment.
Any in sight or valuable thoughts to share are welcomed!
Peace ;]
Thursday, December 18, 2008
*nixes Backup Solution
Sunday, December 14, 2008
FreeBSD ZFS
I have been listening people talking about ZFS, and it is ported to FreeBSD, I don't play with it until today.
It does seem that FreeBSD is getting solarish, ZFS, Dtrace and what else. Anyway here's simple screenshot of mine with ZFS setup -
It does seem that FreeBSD is getting solarish, ZFS, Dtrace and what else. Anyway here's simple screenshot of mine with ZFS setup -

I may spend more time playing with it, if you are interested in ZFS on FreeBSD, you should check out -
http://wiki.freebsd.org/ZFS
By the way, FreeBSD 7.1 RC1 is out, grab it while it's hot!
http://wiki.freebsd.org/ZFS
By the way, FreeBSD 7.1 RC1 is out, grab it while it's hot!
Cheers ;]
Saturday, December 13, 2008
Anonymous Troll
I have previously blogged about my experience in Singapore Govware here, however I don't know I get such interesting comment until I was told by a friend who read it. The comment is written as following -
--------------------------------------------------------------
Anonymous said ....
With all due respect to you and your great work with hex and what not, I'd like to rant a bit. I know its belated, but here goes :)
Sometimes security is not about you 'teaching' people what to do with your l337 NSM toolkit. It is normal for security conferences/events to be a closed door affair or by invitation only. I bet there were some concerns by some parties that you're blackhats/can't_be_trusted/not-really-security-analyst whom they can share information with. So its better late than never to kick you out. The level or kind of stuff you and other l337 friends write at security.org.my also don't help I think.
So get real, be trusted, and stop associating yourself with ppl whose deep insights on security are only by taking screenshots at defacements or error messages, blowing them out of porportion, make kidd1e5 happy and then sell a training program! So don't be disheartened at being kicked out at a per invite only program.
-----------------------------------------------------------
I don't really want to argue anything here, my point here is if you don't know me, don't justify me with your narrow minded like you know me very well, and stop acting like anonymous coward.
--------------------------------------------------------------
Anonymous said ....
With all due respect to you and your great work with hex and what not, I'd like to rant a bit. I know its belated, but here goes :)
Sometimes security is not about you 'teaching' people what to do with your l337 NSM toolkit. It is normal for security conferences/events to be a closed door affair or by invitation only. I bet there were some concerns by some parties that you're blackhats/can't_be_trusted/not-really-security-analyst whom they can share information with. So its better late than never to kick you out. The level or kind of stuff you and other l337 friends write at security.org.my also don't help I think.
So get real, be trusted, and stop associating yourself with ppl whose deep insights on security are only by taking screenshots at defacements or error messages, blowing them out of porportion, make kidd1e5 happy and then sell a training program! So don't be disheartened at being kicked out at a per invite only program.
-----------------------------------------------------------
I don't really want to argue anything here, my point here is if you don't know me, don't justify me with your narrow minded like you know me very well, and stop acting like anonymous coward.
Peace ;]
What Am I Doing?
I hardly blog these days, and have been busy with current works plus my own fun research. It's about the end of year 2008 and I figure life is more challenging when I'm getting older.
raWPacket is currently in the state of "slowing down" or you can call it slacking, so we will restart our engine next year(2009). Hopefully we can get many interesting projects done in coming year, some are on the way!
It's been couple of months working for GE now, thanks to my friend - Richard Bejtlich for the opportunity, faithfully. For the other guys I'm working with, you guys are always rocking!
For my own research, lets keep it secret for now, it will be revealed soon.
raWPacket is currently in the state of "slowing down" or you can call it slacking, so we will restart our engine next year(2009). Hopefully we can get many interesting projects done in coming year, some are on the way!
It's been couple of months working for GE now, thanks to my friend - Richard Bejtlich for the opportunity, faithfully. For the other guys I'm working with, you guys are always rocking!
For my own research, lets keep it secret for now, it will be revealed soon.
Cheers ;]
Monday, December 01, 2008
Drunken Monkey: Running Network Miner with Wine
Network-Based Forensics is emerging now, we are seeing more and more NBF tools in active development now, one of the decent NBF tool I would like to mention here is NetworkMiner which is developed by Erik Hjelmvik. NetworkMiner is developed using .net framework, therefore it has Windows version only, I will show you how you can get it running using Wine on *nix based OS especially Ubuntu Linux.
Installing Wine -
shell>sudo apt-get install wine wine-dev cabextract
Configure Wine -
shell>winecfg
In Application tab, change windows version to Windows 2000
shell>wget http://kegel.com/wine/winetricks
Install cofefronts and .net framework 2.0 -
shell>sh winetricks corefonts dotnet20
Download NetworkMiner -
Unzip it and run -
shell>wine NetworkMiner.exe
Here you go -
Installing Wine -
shell>sudo apt-get install wine wine-dev cabextract
Configure Wine -
shell>winecfg
In Application tab, change windows version to Windows 2000
shell>wget http://kegel.com/wine/winetricks
Install cofefronts and .net framework 2.0 -
shell>sh winetricks corefonts dotnet20
Download NetworkMiner -
shell>wget \
http://sourceforge.net/project/showfiles.php?group_id=189429
http://sourceforge.net/project/showfiles.php?group_id=189429
Unzip it and run -
shell>wine NetworkMiner.exe
Here you go -


Cheers (;])
Wednesday, November 26, 2008
Network-Based Forensics: Xplico

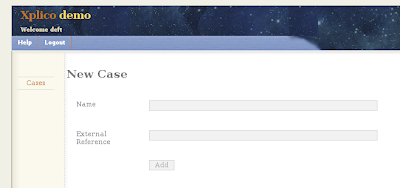
If you are interested in Network-Based Forensics, you should give this tool a try - Xplico, this tool is quite promising and in active development.
During HITB Training and Conference, I have mentioned about the challenge and problem with Network-Based Forensics, one of them is the lack of protocol dissectors(especially application layer). Looking at Xplico roadmap, you can see they are trying to add more and more dissectors to be more advance in traffic reconstruction(you can't really base on tcp itself as the session itself is mostly handled by the application layer these days).
Xplico is definitely designed for Network-Based Forensics only, and it follows file system forensics approach where you can create case and extract data from the pcap. There are few things I would like to see it in Xplico if possible -
1. Support more packet format(or conversion)
2. Better search engine(not only email)
3. Report generation
4. Data export to various format
5. Per host traffic information
If you are interested in trying out Xplico quickly, you can check out Deft liveCD.
More screenshots!!!!!
During HITB Training and Conference, I have mentioned about the challenge and problem with Network-Based Forensics, one of them is the lack of protocol dissectors(especially application layer). Looking at Xplico roadmap, you can see they are trying to add more and more dissectors to be more advance in traffic reconstruction(you can't really base on tcp itself as the session itself is mostly handled by the application layer these days).
Xplico is definitely designed for Network-Based Forensics only, and it follows file system forensics approach where you can create case and extract data from the pcap. There are few things I would like to see it in Xplico if possible -
1. Support more packet format(or conversion)
2. Better search engine(not only email)
3. Report generation
4. Data export to various format
5. Per host traffic information
If you are interested in trying out Xplico quickly, you can check out Deft liveCD.
More screenshots!!!!!

Enjoy ;]
Thursday, October 30, 2008
HeX In The Box
We release the HeX special edition for HITB Security Conference, the theme we use is HeX In The Box. If you are the HITB Conference participant, you might or might not get the CD we distribute in the first day of conference as we only have about 120 pieces of them so it is really limited.
This special edition comes with new wallpaper and cd sticker as well. Thanks to Vickson for the comic style of design this time!
This special edition comes with new wallpaper and cd sticker as well. Thanks to Vickson for the comic style of design this time!
Saturday, October 18, 2008
Bro 1.4: Eating Netflow
 The new Bro can import NetFlow version 5 data now, if you are using HeX 2.0, you can test it quickly. Here's how you can test its new ability to work with NetFlow.
The new Bro can import NetFlow version 5 data now, if you are using HeX 2.0, you can test it quickly. Here's how you can test its new ability to work with NetFlow.Using fprobe to export NetFlow version 5 data on network interface le0 to address 127.0.0.1 and port 5555 -
shell>sudo fprobe -n 5 -f ip -i le0 127.0.0.1:5555
Using bro to eat NetFlow data and log them to disk -
shell>sudo bro --netflow 127.0.0.1:5555 HeX netflow
You will find netflow.log in your $BROLOGS directory, and you can simply examine them with any text viewer.
I'm going to distribute bro-1.4 binary that works well with HeX so that people can try them out if they are interested in latest Bro offerings.
Enjoy (;])
HITB 2008 and Our Technical Training

HackInTheBox Security Conference 2008 in Malaysia is around the corner, this time we are going to bring you triple tracks which will be running simultaneously at the same time and participants are allowed to join any track they like to. Plus we have great speakers line up.
The old and useless CTF organizing team will retire this time and be replaced by the new bloods, so we hope they are doing the best they can to get the game going. On the other hand, there will be OpenHack as usual. We also hope you are going to enjoy HITB Lab which will be running for the first time ever.
For the moment, me and spoonfork are updating our training materials, just like previous training, our training goes with the name "Structured Network Threat Analysis & Forensics". However we are changing strategy and bringing new stuffs. Besides Network Security Monitoring, we are going to focus more on Network Based Forensics and its challenges. We also include exercises so that participants can get the feel of it during the training session.
If you haven't registered yet, I think you should. You can check out the price of registration and it's real cheap. Don't miss the chance to learn about latest security issues, meet the world class security professionals and get to know local talents around!
Cheers ;]
The old and useless CTF organizing team will retire this time and be replaced by the new bloods, so we hope they are doing the best they can to get the game going. On the other hand, there will be OpenHack as usual. We also hope you are going to enjoy HITB Lab which will be running for the first time ever.
For the moment, me and spoonfork are updating our training materials, just like previous training, our training goes with the name "Structured Network Threat Analysis & Forensics". However we are changing strategy and bringing new stuffs. Besides Network Security Monitoring, we are going to focus more on Network Based Forensics and its challenges. We also include exercises so that participants can get the feel of it during the training session.
If you haven't registered yet, I think you should. You can check out the price of registration and it's real cheap. Don't miss the chance to learn about latest security issues, meet the world class security professionals and get to know local talents around!
Cheers ;]
Bro: 1.4 Release
 Kudos again to Bro development team for making the release of version 1.4. This release has included tons of new features and also tons of bug fixes.
Kudos again to Bro development team for making the release of version 1.4. This release has included tons of new features and also tons of bug fixes.I'm looking forward to try out things like NetFlow, Time Machine and many others. If you are interested in Bro, grab the latest version while it's hot. You can download it at -
http://bro-ids.org/download.html
The detail changes can be read here.
Enjoy ;]
Friday, October 10, 2008
Foss.my 2008
Many friends in OSS circle have already blogged about this, so I won't repeat anything much, if you are interested in Foss, and you are in Malaysia, this is definitely the event that you should come.
For more information, look here ->
http://foss.my/
Enjoy ;]
Expanding Response: Deeper Analysis
My friend Russ McRee just published a paper called Expanding Response: Deeper Analysis for Incident Handlers with SANS for his GCIH Gold cert that includes details on Argus, HeX, NSM-console, and NetworkMiner using content from the original ISSA articles as well as current updates.
You can find his paper here -
http://www.sans.org/reading_room/whitepapers/incident/32904.php
Nice work Russ!
Cheers ;]
Wednesday, October 08, 2008
Govware: Positive Security?
Few months ago, Dhillon(HITB Founder) told us about Govware which is organized by Ministry Of Home Affairs Singapore and they invited us to their conference.
So HITB is invited to Singapore Govware, and we were quite looking forward to this event as we are told Singapore is first world country and they are great in event organizing. Unfortunately this time, we are going down to Singapore with our own budget(Other events' organizers pay our accomodation for our effort) but we thought since it's just our neighbor country, lets pay on our own.
So we are being supportive to run Web Hacking Challenge for Govware as well(Rufio handles this), me and Mel are also invited to give talk in closed door - Law Enforcement Track to share our knowledge with the audience. In the first day of event, everything goes smoothly. Me and mel are presenting 8 Layers Of Security and performing Network Forensics using HeX 2.0 that we have just released few days ago. We are glad to know some of people who are working in law enforcement units.
So I don't want to comment much about other presentations since I don't really listen to them as we are not allowed to, but we still managed to listen to 3 talks which are also closed door since their people never block us. But then again, we were banned from the room after their clueless dudes figure out we were in the talk, they should have blocked us from going in instead of asking us out in the middle of the presentation.
So nothing much happening in the first day of event except this shit, we went back to apartment and grabbed our dinner.
So today(second day of Govware) we went to the venue, and we just started running Web Hacking Challenge, as usual all of us are wearing HITB t-shirt to present who we are. Then out of sudden, there's some "don't know who"(probably fear to lose(kiasu) organizer) came to us, and informed us that we are not allowed to deliver our HITB conference fliers, we can't promote our HITB Conference in overt style(I don't get this, we just deliver our flier for whoever passes by our booth like everybody else instead of doing it aggresively) and we are also prohibited to wear our own HITB t-shirt as well(but we see others can wear their own company t-shirt(hint: Splunk) and they are not abused.
So what should we do now after coming down all the way from Kuala Lumpur to this Govware Singapore? Absolutely nothing but get out of this crap place. And Govware is promoting Positive Security but can't even allow us to inform the audience about another security conference with world class security experts in neighbor country(to be honest our conference are totally different than Govware as we are emphasizing more on new attack mechanisms and more technical oriented).
So to conclude this, we are now enlightened of how thisso called "First World Country" Ministry people manages international event, with unfair treatment where other companies can do their "not so overt" marketing(because they are sponsors?), they can wear their own company t-shirt, but we are asked to fuck off!
So this is definitely great job from them, and thanks for the awful invitation, you can fuck off now. Kudos!
So Enjoyable ;]
So HITB is invited to Singapore Govware, and we were quite looking forward to this event as we are told Singapore is first world country and they are great in event organizing. Unfortunately this time, we are going down to Singapore with our own budget(Other events' organizers pay our accomodation for our effort) but we thought since it's just our neighbor country, lets pay on our own.
So we are being supportive to run Web Hacking Challenge for Govware as well(Rufio handles this), me and Mel are also invited to give talk in closed door - Law Enforcement Track to share our knowledge with the audience. In the first day of event, everything goes smoothly. Me and mel are presenting 8 Layers Of Security and performing Network Forensics using HeX 2.0 that we have just released few days ago. We are glad to know some of people who are working in law enforcement units.
So I don't want to comment much about other presentations since I don't really listen to them as we are not allowed to, but we still managed to listen to 3 talks which are also closed door since their people never block us. But then again, we were banned from the room after their clueless dudes figure out we were in the talk, they should have blocked us from going in instead of asking us out in the middle of the presentation.
So nothing much happening in the first day of event except this shit, we went back to apartment and grabbed our dinner.
So today(second day of Govware) we went to the venue, and we just started running Web Hacking Challenge, as usual all of us are wearing HITB t-shirt to present who we are. Then out of sudden, there's some "don't know who"(probably fear to lose(kiasu) organizer) came to us, and informed us that we are not allowed to deliver our HITB conference fliers, we can't promote our HITB Conference in overt style(I don't get this, we just deliver our flier for whoever passes by our booth like everybody else instead of doing it aggresively) and we are also prohibited to wear our own HITB t-shirt as well(but we see others can wear their own company t-shirt(hint: Splunk) and they are not abused.
So what should we do now after coming down all the way from Kuala Lumpur to this Govware Singapore? Absolutely nothing but get out of this crap place. And Govware is promoting Positive Security but can't even allow us to inform the audience about another security conference with world class security experts in neighbor country(to be honest our conference are totally different than Govware as we are emphasizing more on new attack mechanisms and more technical oriented).
So to conclude this, we are now enlightened of how thisso called "First World Country" Ministry people manages international event, with unfair treatment where other companies can do their "not so overt" marketing(because they are sponsors?), they can wear their own company t-shirt, but we are asked to fuck off!
So this is definitely great job from them, and thanks for the awful invitation, you can fuck off now. Kudos!
So Enjoyable ;]
Monday, October 06, 2008
HeX 2.0 Release - The Bonobo
Today is big day for us as we finally have HeX 2.0 Release - The Bonobo unleashed.
After many months of struggling in both testing and development phases, there are a lot of new features added in this release. To sum it up, we have -
1. FreeBSD 7 Stable
2. Unionfs
3. NSM Console updates
4. Tons of analysis alias and scripts
5. Tons of NSM tools' signatures
6. Firefox - Useful websites bookmark
7. Liferea - Security rss feeds
For more information, you can check out its own site which is located at -
http://www.rawpacket.org/projects/hex/hex-livecd/version-20-release
I would like to say thanks to HeX team members for all the hard works and continuous efforts. You guys are just rocking!!!!!
Enjoy (;])
After many months of struggling in both testing and development phases, there are a lot of new features added in this release. To sum it up, we have -
1. FreeBSD 7 Stable
2. Unionfs
3. NSM Console updates
4. Tons of analysis alias and scripts
5. Tons of NSM tools' signatures
6. Firefox - Useful websites bookmark
7. Liferea - Security rss feeds
For more information, you can check out its own site which is located at -
http://www.rawpacket.org/projects/hex/hex-livecd/version-20-release
I would like to say thanks to HeX team members for all the hard works and continuous efforts. You guys are just rocking!!!!!
Enjoy (;])
Sunday, October 05, 2008
FreeBSD: Pktanon Installation
What is pktanon?
PktAnon performs network trace anonymization. It is highly configurable and uses anonymization profiles.
My friend Richard has actually blogged about it especially for Debian platform.
One of the pktanon main developer - Christoph has emailed me that they have fixed pktanon and make it work on FreeBSD, and I'd like to try it out, I won't make a port for FreeBSD as I'm told that Wesley is working on pktanon port.
But if you are interested, that's how you can get it to work on FreeBSD.
Get the dependencies, install these two FreeBSD ports -
1. boost
2. xerces-c2
We can now perform pktanon installation -
shell>wget \
http://www.tm.uka.de/software/pktanon/download/pktanon-1.2.1-dev.tar.gz
shell>tar xvzf pktanon-1.2.1-dev.tar.gz
shell>cd pktanon-1.2.1-dev
shell>export CFLAGS=-I/usr/local/include
shell>export CPPFLAGS=-I/usr/local/include
shell>export LDFLAGS=-L/usr/local/lib
shell>./configure
shell>make
shell>sudo make install
You can now start working with pktanon, I won't show those as you can check out the information from pktanon website. We will include pktanon in HeX(definitely not HeX 2.0 but maybe 2.0.1 as we already froze the port tree while pktanon port is still not in yet). It's worth to add it as people who would like to contribute to Openpacket need to anonymize their packet trace.
Cheers (;])
PktAnon performs network trace anonymization. It is highly configurable and uses anonymization profiles.
My friend Richard has actually blogged about it especially for Debian platform.
One of the pktanon main developer - Christoph has emailed me that they have fixed pktanon and make it work on FreeBSD, and I'd like to try it out, I won't make a port for FreeBSD as I'm told that Wesley is working on pktanon port.
But if you are interested, that's how you can get it to work on FreeBSD.
Get the dependencies, install these two FreeBSD ports -
1. boost
2. xerces-c2
We can now perform pktanon installation -
shell>wget \
http://www.tm.uka.de/software/pktanon/download/pktanon-1.2.1-dev.tar.gz
shell>tar xvzf pktanon-1.2.1-dev.tar.gz
shell>cd pktanon-1.2.1-dev
shell>export CFLAGS=-I/usr/local/include
shell>export CPPFLAGS=-I/usr/local/include
shell>export LDFLAGS=-L/usr/local/lib
shell>./configure
shell>make
shell>sudo make install
You can now start working with pktanon, I won't show those as you can check out the information from pktanon website. We will include pktanon in HeX(definitely not HeX 2.0 but maybe 2.0.1 as we already froze the port tree while pktanon port is still not in yet). It's worth to add it as people who would like to contribute to Openpacket need to anonymize their packet trace.
Cheers (;])
Thursday, October 02, 2008
HeX 2.0 R: Preview
Saturday, September 27, 2008
HeX 2.0 Release is NEAR
We are going to unleash HeX 2.0 Release, if no major issue found again it should be on next week.
Stay tuned ;]
Saturday, September 20, 2008
Another NSM related blog
Our webmaster guti has his own technical blog, if you are interested in his works, check out -
http://www.gutizz.com/
I learned some tips and tricks about ourmon and grace, though he doesn't blog frequently, but I found his post with quality.
http://www.gutizz.com/
I learned some tips and tricks about ourmon and grace, though he doesn't blog frequently, but I found his post with quality.
Enjoy ;]
Tuesday, September 02, 2008
FreeBSD: Port's Foo
I have learned a few new tricks about using FreeBSD ports which I don't know last time, there you go!
For ports which provides configure options, you can actually configure it via -
shell>make config
To show the configuration -
shell>make showconfig
To remove current configuration, or reset it to default -
shell>make rmconfig
To build the package from port -
shell>make package
To build the package from port for its dependencies as well -
shell>make package-recursive
If you have the port previously installed, and you want to reinstall with different option set, make sure you have the "work" directory deleted in particular port or else the new configure option won't be used.
Enjoy ;]
For ports which provides configure options, you can actually configure it via -
shell>make config
To show the configuration -
shell>make showconfig
To remove current configuration, or reset it to default -
shell>make rmconfig
To build the package from port -
shell>make package
To build the package from port for its dependencies as well -
shell>make package-recursive
If you have the port previously installed, and you want to reinstall with different option set, make sure you have the "work" directory deleted in particular port or else the new configure option won't be used.
Enjoy ;]
Tuesday, August 26, 2008
HeX 021: Decode base64
There are a lot of malicious contents which are actually encoded with base64 to create confusion.
This is just quick one as I have friend asking about it on how to decode base64 encoding. One liner with python -
Or you can use nsm console if you are running HeX -
nsm>decode base64 'encoded strings here'
Enjoy ;]
This is just quick one as I have friend asking about it on how to decode base64 encoding. One liner with python -
shell>python -c "import binascii; \
binascii.a2b_base64('encoded strings here')
binascii.a2b_base64('encoded strings here')
Or you can use nsm console if you are running HeX -
nsm>decode base64 'encoded strings here'
Enjoy ;]
Tuesday, August 19, 2008
HeX 021: Resolving Ihack 2008 password.pcap
My friend ayoi has posted Ihack 2008: Defense Challenge here, I don't really have time to look into the whole game. However I have tried to give it a shot for password.pcap to figure out what's the passphrase.
I decide to use HeX liveCD for this quick challenge since chfl4gs_ has presented it in IHack. Initial look at the traffic -
shell>tcpdump -ttttnnr password.pcap
reading from file /home/analyzt/rp-Analysis/password.pcap, link-type EN10MB (Ethernet)I decide to use HeX liveCD for this quick challenge since chfl4gs_ has presented it in IHack. Initial look at the traffic -
shell>tcpdump -ttttnnr password.pcap
2008-08-14 12:21:11.469308 IP 10.10.3.126.1337 > 10.10.75.1.31337: S 1879048192:1879048192(0) win 512
2008-08-14 12:21:11.469524 IP 10.10.75.1.31337 > 10.10.3.126.1337: R 0:0(0) ack 1879048193 win 0
2008-08-14 12:21:12.212445 IP 10.10.3.126.1337 > 10.10.75.1.31337: S 872415232:872415232(0) win 512
2008-08-14 12:21:12.212549 IP 10.10.75.1.31337 > 10.10.3.126.1337: R 0:0(0) ack 3288334337 win 0
2008-08-14 12:21:12.959563 IP 10.10.3.126.1337 > 10.10.75.1.31337: S 603979776:603979776(0) win 512
2008-08-14 12:21:12.959710 IP 10.10.75.1.31337 > 10.10.3.126.1337: R 0:0(0) ack 3019898881 win 0
2008-08-14 12:21:13.656942 IP 10.10.3.126.1337 > 10.10.75.1.31337: S 889192448:889192448(0) win 512
Output truncated .....
Initial view of the network traffic tells you that the network traffic contains no data transfer, and it is heavily crafted(port). It also hints you that the passphrase should be residing in the packet header. Therefore I start dig into the header by printing it in hex and ascii dump output.
shell>tcpdump -XXttttnnr password.pcap
2008-08-14 12:21:11.469308 IP 10.10.3.126.1337 > 10.10.75.1.31337: S 1879048192:
1879048192(0) win 512
0x0000: 000c 294b dcf1 000c 2945 914a 0800 4500 ..)K....)E.J..E.
0x0010: 0028 5c00 0000 4006 bc3d 0a0a 037e 0a0a .(\...@..=...~..
0x0020: 4b01 0539 7a69 7000 0000 0000 0000 5002 K..9zip.......P.
0x0030: 0200 5bad 0000 ..[...
2008-08-14 12:21:11.469524 IP 10.10.75.1.31337 > 10.10.3.126.1337: R 0:0(0) ack
1879048193 win 0
0x0000: 000c 2945 914a 000c 294b dcf1 0800 4500 ..)E.J..)K....E.
0x0010: 0028 0000 4000 4006 d83d 0a0a 4b01 0a0a .(..@.@..=..K...
0x0020: 037e 7a69 0539 0000 0000 7000 0001 5014 .~zi.9....p...P.
0x0030: 0000 5d9a 0000 ..]...
2008-08-14 12:21:12.212445 IP 10.10.3.126.1337 > 10.10.75.1.31337: S 872415232:8
72415232(0) win 512
0x0000: 000c 294b dcf1 000c 2945 914a 0800 4500 ..)K....)E.J..E.
0x0010: 0028 2000 0000 4006 f83d 0a0a 037e 0a0a .(....@..=...~..
0x0020: 4b01 0539 7a69 3400 0000 0000 0000 5002 K..9zi4.......P.
0x0030: 0200 97ad 0000 ......
2008-08-14 12:21:12.212549 IP 10.10.75.1.31337 > 10.10.3.126.1337: R 0:0(0) ack
3288334337 win 0
0x0000: 000c 2945 914a 000c 294b dcf1 0800 4500 ..)E.J..)K....E.
0x0010: 0028 0000 4000 4006 d83d 0a0a 4b01 0a0a .(..@.@..=..K...
0x0020: 037e 7a69 0539 0000 0000 3400 0001 5014 .~zi.9....4...P.
0x0030: 0000 999a 0000 ......
Output truncated .....
When comes to examing the packet header, it's best to look at the pattern, and realizing that some fields are usually static in this case helps you to identify the different, if we look at the 4 packets above, you may spot
10.10.3.126 -> 10.10.75.1 - tcp sequence number
10.10.75.1 -> 10.10.3.126 - tcp acknowledge number(tcp sequence number + 1)
10.10.3.126 -> 10.10.75.1 - tcp sequence number
10.10.75.1 -> 10.10.3.126 - tcp acknowledge number(tcp sequence number + 1)
So to get the answer, you can just print the connection from one side(from 10.10.3.126 to 10.10.75.1) -
shell>tcpdump -XXttttnnr password.pcap ip src 10.10.3.126
2008-08-14 12:21:11.469308 IP 10.10.3.126.1337 > 10.10.75.1.31337: S 1879048192:
1879048192(0) win 512
0x0000: 000c 294b dcf1 000c 2945 914a 0800 4500 ..)K....)E.J..E.
0x0010: 0028 5c00 0000 4006 bc3d 0a0a 037e 0a0a .(\...@..=...~..
0x0020: 4b01 0539 7a69 7000 0000 0000 0000 5002 K..9zip.......P.
0x0030: 0200 5bad 0000 ..[...
2008-08-14 12:21:12.212445 IP 10.10.3.126.1337 > 10.10.75.1.31337: S 872415232:8
72415232(0) win 512
0x0000: 000c 294b dcf1 000c 2945 914a 0800 4500 ..)K....)E.J..E.
0x0010: 0028 2000 0000 4006 f83d 0a0a 037e 0a0a .(....@..=...~..
0x0020: 4b01 0539 7a69 3400 0000 0000 0000 5002 K..9zi4.......P.
0x0030: 0200 97ad 0000 ......
2008-08-14 12:21:12.959563 IP 10.10.3.126.1337 > 10.10.75.1.31337: S 603979776:6
03979776(0) win 512
0x0000: 000c 294b dcf1 000c 2945 914a 0800 4500 ..)K....)E.J..E.
0x0010: 0028 6200 0000 4006 b63d 0a0a 037e 0a0a .(b...@..=...~..
0x0020: 4b01 0539 7a69 2400 0000 0000 0000 5002 K..9zi$.......P.
0x0030: 0200 a7ad 0000 ......
2008-08-14 12:21:13.656942 IP 10.10.3.126.1337 > 10.10.75.1.31337: S 889192448:8
89192448(0) win 512
0x0000: 000c 294b dcf1 000c 2945 914a 0800 4500 ..)K....)E.J..E.
0x0010: 0028 8d00 0000 4006 8b3d 0a0a 037e 0a0a .(....@..=...~..
0x0020: 4b01 0539 7a69 3500 0000 0000 0000 5002 K..9zi5.......P.
0x0030: 0200 96ad 0000 ......
Output truncated .....
If you want to see another side of the traffic, just tune the bpf filter to ip src 10.10.75.1, however for that you will need to look at the acknowledge number. You should have the answer now.
Anyway when comes to print certain field in the header, you can use tshark(part of wireshark), and force it to print certain field, for example -
Anyway when comes to print certain field in the header, you can use tshark(part of wireshark), and force it to print certain field, for example -
shell>tshark -Tfields -e 'tcp.seq' -nr password.pcap -o tcp.relative_sequence_numbers:FALSE -R 'ip.src == 10.10.3.126'
1879048192
872415232
603979776
889192448
1996488704
805306368
1912602624
1677721600
536870912
822083584
889192448
536870912
822083584
838860800
855638016
167772160
That's your answer in decimal, you can convert the number to hex and from hex to ascii. Using pythong quickies -
Decimal to Hex -
shell>python -c 'print hex()'
HeX to Ascii
shell>python -c 'import binascii; print binascii.a2b_hex("")'
You should have the passphrase to unrar Questions.rar
shell>unrar e Questions.rar
Bump in the passphrase and you will be able to retrieve all the files you need.
During the challenge event, I don't see any participants use HeX for this purpose. And lot of them just use wireshark to examine, my opinion is using wireshark is not effective in this scenario as wireshark is great when you want to do per packet examination or dealing with network protocols you are not familiar with. However for this, I would say tcpdump and tshark are more effective tools to obtain the clue.
Enjoy (;])
Monday, August 18, 2008
Little note about GDB
This is just for myself as I'm not the guy who uses debugger much. However sometimes it helps when you have core dump for the program you are running. This is simple one of what you can examine with the core dump file.
shell>gdb bro bro.core
GNU gdb 6.1.1 [FreeBSD]
Copyright 2004 Free Software Foundation, Inc.
GDB is free software, covered by the GNU General Public License, and you are
welcome to change it and/or distribute copies of it under certain conditions.
Type "show copying" to see the conditions.
There is absolutely no warranty for GDB. Type "show warranty" for details.
This GDB was configured as "i386-marcel-freebsd"...
Core was generated by `bro'.
Program terminated with signal 11, Segmentation fault.
Reading symbols from /usr/lib/libmagic.so.3...done.
Loaded symbols for /usr/lib/libmagic.so.3
Reading symbols from /lib/libz.so.4...done.
Loaded symbols for /lib/libz.so.4
Reading symbols from /usr/lib/libssl.so.5...done.
Loaded symbols for /usr/lib/libssl.so.5
Reading symbols from /lib/libcrypto.so.5...done.
Loaded symbols for /lib/libcrypto.so.5
Reading symbols from /lib/libncurses.so.7...done.
Loaded symbols for /lib/libncurses.so.7
Reading symbols from /usr/lib/libstdc++.so.6...done.
Loaded symbols for /usr/lib/libstdc++.so.6
Reading symbols from /lib/libm.so.5...done.
Loaded symbols for /lib/libm.so.5
Reading symbols from /lib/libgcc_s.so.1...done.
Loaded symbols for /lib/libgcc_s.so.1
Reading symbols from /lib/libc.so.7...done.
Loaded symbols for /lib/libc.so.7
Reading symbols from /libexec/ld-elf.so.1...done.
Loaded symbols for /libexec/ld-elf.so.1
#0 0x080518ef in copy_string () at SSLInterpreter.cc:30
30 */
(gdb) print copy_string
$1 = {} 0x80518d0
(gdb) bt
#0 0x080518ef in copy_string () at SSLInterpreter.cc:30
#1 0x0809e249 in DNS_Mapping (this=0x843e6c8,
host=0x810e00c1 , h=0x830c0d0)
at DNS_Mgr.cc:171
#2 0x080a049f in DNS_Mgr::AddResult (this=0x830bd68, dr=0x843e210,
r=0xbfbf9070) at DNS_Mgr.cc:697
#3 0x080a08d6 in DNS_Mgr::Resolve (this=0x830bd68) at DNS_Mgr.cc:601
#4 0x080a0edd in DNS_Mgr::LookupHost (this=0x830bd68,
name=0x843398e "l.root-servers.net") at DNS_Mgr.cc:485
#5 0x0806826a in brolex () at scan.l:330
#6 0x08053d5c in yyparse () at p.c:2277
#7 0x0804efb6 in main (argc=5, argv=0xbfbfebac) at main.cc:751
(gdb) up
#1 0x0809e249 in DNS_Mapping (this=0x843e6c8,
host=0x810e00c1 , h=0x830c0d0)
at DNS_Mgr.cc:171
171 req_host = copy_string(host);
I'm still learning how to interpret them correctly, hopefully more to come.
Cheers ;]
shell>gdb bro bro.core
GNU gdb 6.1.1 [FreeBSD]
Copyright 2004 Free Software Foundation, Inc.
GDB is free software, covered by the GNU General Public License, and you are
welcome to change it and/or distribute copies of it under certain conditions.
Type "show copying" to see the conditions.
There is absolutely no warranty for GDB. Type "show warranty" for details.
This GDB was configured as "i386-marcel-freebsd"...
Core was generated by `bro'.
Program terminated with signal 11, Segmentation fault.
Reading symbols from /usr/lib/libmagic.so.3...done.
Loaded symbols for /usr/lib/libmagic.so.3
Reading symbols from /lib/libz.so.4...done.
Loaded symbols for /lib/libz.so.4
Reading symbols from /usr/lib/libssl.so.5...done.
Loaded symbols for /usr/lib/libssl.so.5
Reading symbols from /lib/libcrypto.so.5...done.
Loaded symbols for /lib/libcrypto.so.5
Reading symbols from /lib/libncurses.so.7...done.
Loaded symbols for /lib/libncurses.so.7
Reading symbols from /usr/lib/libstdc++.so.6...done.
Loaded symbols for /usr/lib/libstdc++.so.6
Reading symbols from /lib/libm.so.5...done.
Loaded symbols for /lib/libm.so.5
Reading symbols from /lib/libgcc_s.so.1...done.
Loaded symbols for /lib/libgcc_s.so.1
Reading symbols from /lib/libc.so.7...done.
Loaded symbols for /lib/libc.so.7
Reading symbols from /libexec/ld-elf.so.1...done.
Loaded symbols for /libexec/ld-elf.so.1
#0 0x080518ef in copy_string () at SSLInterpreter.cc:30
30 */
(gdb) print copy_string
$1 = {
(gdb) bt
#0 0x080518ef in copy_string () at SSLInterpreter.cc:30
#1 0x0809e249 in DNS_Mapping (this=0x843e6c8,
host=0x810e00c1 , h=0x830c0d0)
at DNS_Mgr.cc:171
#2 0x080a049f in DNS_Mgr::AddResult (this=0x830bd68, dr=0x843e210,
r=0xbfbf9070) at DNS_Mgr.cc:697
#3 0x080a08d6 in DNS_Mgr::Resolve (this=0x830bd68) at DNS_Mgr.cc:601
#4 0x080a0edd in DNS_Mgr::LookupHost (this=0x830bd68,
name=0x843398e "l.root-servers.net") at DNS_Mgr.cc:485
#5 0x0806826a in brolex () at scan.l:330
#6 0x08053d5c in yyparse () at p.c:2277
#7 0x0804efb6 in main (argc=5, argv=0xbfbfebac) at main.cc:751
(gdb) up
#1 0x0809e249 in DNS_Mapping (this=0x843e6c8,
host=0x810e00c1 , h=0x830c0d0)
at DNS_Mgr.cc:171
171 req_host = copy_string(host);
I'm still learning how to interpret them correctly, hopefully more to come.
Cheers ;]
Saturday, August 16, 2008
FreeBSD: Bpfstat is in Netstat
My friend Richard(Taosecurity) has blogged about bpfstat here, and for now bpfstat is already ported as part of netstat in FreeBSD 7. You can run the netstat with -B option -
shell>netstat -B -I le0
Pid Netif Flags Recv Drop Match Sblen Hblen Commandshell>netstat -B -I le0
820 le0 p--s--- 989344 0 958346 0 0 bro
761 le0 p--s--- 989444 0 989444 216 0 argus
754 le0 p--s--- 410 0 410 1392 0 ourmon
330 le0 -ifs--l 989458 0 440 0 0 dhclient
As you can see it is very useful when comes to monitor the libpcap based tools, however there's one feature I miss during the time I use bpfstat which is -i(interval of wait second to report). To simulate similar function, I have found a simple way by using infinite loops -
shell>z=1; while [ $z -eq 1 ]; do netstat -B -I le0; sleep 3; done
This way it will report every 3 seconds(sleep 3), and if you just want to monitor particular tools, use grep will do.
Cheers ;]
shell>z=1; while [ $z -eq 1 ]; do netstat -B -I le0; sleep 3; done
This way it will report every 3 seconds(sleep 3), and if you just want to monitor particular tools, use grep will do.
Cheers ;]
Wednesday, August 06, 2008
HeX 2.0 RC1 is now
After long time development, we have finally reached the stage where we are brave enough to release version 2 of HeX, Release Candidate 1. This is the first public version for HeX 2.0 and we hope that by releasing this, people who are interested in it can help testing out this version. I won't be mentioning the new features that we are adding to HeX 2 here as I will put up all the information once we reach the 2.0 Release instead of RC. For the moment, we need people to test all the applications that we have added, a lot of them can be accessed via fluxbox menu so please help in testing.
Currently there are few known problems -
- Netdude is broken
- Autopsy is broken(sleuthkit issue)
- Gvim is broken(font not available)
- Flowtag is broken(Looking for older version of tk while new one is installed)
- NSM Console(Snort module where wrong path is defined in snort configuration file)
- Silktools(Flowcap and Rwflowpack)
- Ragraph is broken
- Zsh is missing
Most of the issues are already fixed in the development repository, therefore don't report to us if you encounter similar problem in HeX 2.0 RC1. If you encounter any other issues, please do report to us via mailing list -
http://groups.google.com/group/HeX-liveCD
Anyway here's the HeX 2.0 RC1 iso -
http://my.rawpacket.org/hex-i386-2.0-RC1-20080803.iso
http://my.rawpacket.org/hex-i386-2.0-RC1-20080803.iso.md5
http://my.rawpacket.org/hex-i386-2.0-RC1-20080803.iso.sha256
Alternatively, you can download from US mirror -
http://us.rawpacket.org/image/hex-i386-2.0-RC1-20080803.iso
Currently there are few known problems -
- Netdude is broken
- Autopsy is broken(sleuthkit issue)
- Gvim is broken(font not available)
- Flowtag is broken(Looking for older version of tk while new one is installed)
- NSM Console(Snort module where wrong path is defined in snort configuration file)
- Silktools(Flowcap and Rwflowpack)
- Ragraph is broken
- Zsh is missing
Most of the issues are already fixed in the development repository, therefore don't report to us if you encounter similar problem in HeX 2.0 RC1. If you encounter any other issues, please do report to us via mailing list -
http://groups.google.com/group/HeX-liveCD
Anyway here's the HeX 2.0 RC1 iso -
http://my.rawpacket.org/hex-i386-2.0-RC1-20080803.iso
http://my.rawpacket.org/hex-i386-2.0-RC1-20080803.iso.md5
http://my.rawpacket.org/hex-i386-2.0-RC1-20080803.iso.sha256
Alternatively, you can download from US mirror -
http://us.rawpacket.org/image/
Thanks to all the raWPacket members who have put the effort in HeX 2.0 development, you guys are walys rocking!
Enjoy (;])
Enjoy (;])
Monday, July 21, 2008
Unimas: Open Source Security Tools Talks

First of all, thanks for the invitation from Unimas, and En. Ahmad who has put the effort to make it happen, me and Mel will be going to University Malaysia Sarawak (Unimas) tomorrow to give talks about Open Source Security Tools and how it can be very useful, either for corporate, or educational environment.
If you are interested in the topic, and you are currently studying in Unimas. Feel free to join us!
If you are interested in the topic, and you are currently studying in Unimas. Feel free to join us!
Enjoy ;]
Tuesday, July 15, 2008
Ubuntu: Netdude Manual Installation
I use netdude for pcap file editing, it's simple and straightforward since it is gui based, however the ubuntu package is rather old(0.3.x) and I need to use the latest version, here's quick way to get the latest version of netdude installed on Ubuntu 8.04.
Download the latest version of netdude, libpcapnav and libnetdude from here -
http://netdude.sourceforge.net/download.html
Then install all the necessary packages -
shell>sudo apt-get install stow
shell>sudo apt-get install build-essential
shell>sudo apt-get install libgtk1.2-dev
shell>sudo apt-get install libpcap0.7-dev
Decompress netdude, libpcapnav and libnetdude, and install them following the sequence - libpcapnav, libnetdude and netdude. It should be prety quick to get it done.
Enjoy ;]
Download the latest version of netdude, libpcapnav and libnetdude from here -
http://netdude.sourceforge.net/download.html
Then install all the necessary packages -
shell>sudo apt-get install stow
shell>sudo apt-get install build-essential
shell>sudo apt-get install libgtk1.2-dev
shell>sudo apt-get install libpcap0.7-dev
Decompress netdude, libpcapnav and libnetdude, and install them following the sequence - libpcapnav, libnetdude and netdude. It should be prety quick to get it done.
Enjoy ;]
Sunday, July 13, 2008
EmergingBro: HowTo
First of all, make sure you have Bro installed on your machine, or you can download it at http://bro-ids.org. If you are using HeX, Bro is installed by default. Once installed, you may find the directory structure of Bro looks like this -
shell>ls -la
total 34shell>ls -la
drwxr-xr-x 15 analyzt wheel 512 Jul 10 17:36 ./
drwxr-xr-x 3 root wheel 512 Jul 10 07:51 ../
drwxr-xr-x 2 analyzt wheel 512 Jul 10 07:51 archive/
drwxr-xr-x 2 analyzt wheel 512 Jul 10 17:35 bin/
drwxr-xr-x 2 analyzt wheel 512 Jul 10 17:39 etc/
drwxr-xr-x 2 analyzt wheel 512 Jul 10 17:35 include/
drwxr-xr-x 2 analyzt wheel 512 Jul 10 17:35 lib/
drwxr-xr-x 3 analyzt wheel 1024 Jul 10 18:01 logs/
drwxr-xr-x 3 analyzt wheel 512 Jul 10 17:36 perl/
drwxr-xr-x 3 analyzt wheel 5120 Jul 10 17:59 policy/
drwxr-xr-x 2 analyzt wheel 512 Jul 10 07:51 reports/
drwxr-xr-x 2 analyzt wheel 512 Jul 10 17:36 scripts/
drwxr-xr-x 4 analyzt wheel 512 Jul 10 07:51 share/
drwxr-xr-x 2 analyzt wheel 512 Jul 11 22:50 site/
drwxr-xr-x 2 analyzt wheel 512 Jul 10 07:51 var/
Please take note on few important directories -
policy directory contains all the policy and analysis scripts with the file extension .bro.
site directory contains site policy files which you can define or configure for specific site.
logs directory contains all the log files that are generated by bro.
etc directory contains bro configuration files, for start up and bro environment variable settings.
Obtain the latest signatures from Emerging Bro -
policy directory contains all the policy and analysis scripts with the file extension .bro.
site directory contains site policy files which you can define or configure for specific site.
logs directory contains all the log files that are generated by bro.
etc directory contains bro configuration files, for start up and bro environment variable settings.
Obtain the latest signatures from Emerging Bro -
shell>cvs -d:pserver:anonymous@cvs.emergingthreats.net:/cvsroot/bro co emerging-bro
shell>cd emerging-bro
shell>ls -l
total 14shell>cd emerging-bro
shell>ls -l
drwxr-xr-x 7 analyzt wheel 512 Jul 10 07:58 ./
drwxr-xr-x 4 analyzt wheel 512 Jul 10 07:55 ../
drwxr-xr-x 2 analyzt wheel 512 Jul 10 11:23 CVS/
drwxr-xr-x 3 analyzt wheel 512 Jul 10 07:58 CVSROOT/
drwxr-xr-x 3 analyzt wheel 1024 Jul 10 18:24 rules/
drwxr-xr-x 4 analyzt wheel 512 Jul 10 18:28 scripts/
drwxr-xr-x 17 analyzt wheel 512 Jul 10 11:23 sigs/
sigs directory contains all the individual signature in different category
rules directory contains main signature file for each category. For example emerging-bro-malware.sig contains all the signatures for MALWARE category.
scripts directory contains all the policy and analysis scripts that are contributed by the community members.
To perform quick test, you can use invoke the signature file using command line option -
Set Bro environment variables -
shell>. bro.cfg
Execute Bro -
shell>bro -s emerging-bro-all.sig -r whatever.pcap `hostname`
If you plan to run it in long term, it's best to edit the file generated during make install-brolite. The file name starts with your hostname, for example it is raWPacket.bro in HeX liveCD since my hostname is raWPacket. Just edit the following section in the file -
-----------------------------------------------------------------------
# To run signatures, uncomment the following line.
# @load brolite-sigs
@ifdef ( use_signatures )
# Load Bro signatures. This is the default file containing Bro
# signatures.
redef signature_files += "signatures";
@endif
-----------------------------------------------------------------------
To this -
@load brolite-sigs
redef signature_files += "emerging-bro-all.sig"
Please do note that other policy scripts must be loaded in order to have signatures invoked properly especially brolite.bro.
Enjoy ;]
Wednesday, July 09, 2008
DefCraft: Official Launching
 After long consideration, I decide to start a company that focuses on security research, development and consultancy. The company name is straightforward - Defensive Craft (DefCraft).
After long consideration, I decide to start a company that focuses on security research, development and consultancy. The company name is straightforward - Defensive Craft (DefCraft).The company offers a wide range of consulting services for specific domains, here's the list -
- Network and Web Application Security Assessment
- Network Security Architecture Planning & Deployment
- Network Security Monitoring Implementation
- Network Security Architecture Auditing
- Network Device Testing & Evaluation
- Network Based Forensics
- Network Profiling Operation
- Incident Response & Handling
- Digital Security Training
If you have any inquiry, please feel free to contact me.
Contact Number: 016 415 9873
Contact Email: defcraft at gmail dot com
For more information, you can check out at -
http://www.defcraft.net
The company has its own blog too which we will blog about what we do behind the lab -
http://blog.defcraft.net
On the other hand, I will still contribute my free time to various open source projects that I'm working on since this is part of company principle I'm emphasizing.
Contact Number: 016 415 9873
Contact Email: defcraft at gmail dot com
For more information, you can check out at -
http://www.defcraft.net
The company has its own blog too which we will blog about what we do behind the lab -
http://blog.defcraft.net
On the other hand, I will still contribute my free time to various open source projects that I'm working on since this is part of company principle I'm emphasizing.
Saturday, July 05, 2008
Emerging Bro
I'm sured not many have heard of Bro comparing to Snort in NIDS arsenal, while both are actually applying different approach in intrusion detection, they are the Open Source NIDS I like to use to complement each others in different setup and deployment.
I'm now working closely with Matt Jonkman from EmergingThreats(ET) to start the new project calls Emerging-Bro, basically the project is about converting set of latest signatures from Snort to Bro so that Bro operators can take advantage of it. You can find more information from the announcement here -
http://www.emergingthreats.net/content/view/80/1/
If you are Bro operators, you might have question of why I'm doing this as Bro is more focused on policy and analysis script development to detect network event(be it normal or abnormal) instead of relying on signatures matching in byte stream. There are reasons why I'm doing this and I'm going to explain here -
Edge
Emerging-Bro will only focus on latest or critical signatures from ET, therefore the project is basically more concerning about latest/critical attacks because most networks are more vulnerable to newly discovered attacks than the old one, therefore detecting and preventing them at network boundary is much important. Currently there are about 100 latest signatures converted from ET to Emerging-Bro, and if you think certain Snort signature should be included, please do let me know.
Leverage
The signature set that is developed by EmergingThreats usually give little time window for attacker and reduce the outbreak period significantly, hence you can pretty quick in detecting initial stage of new attacks. Bro operators can take advantage of this if they can monitor the new attack in time and quickly develope more complete detection scheme with Bro policy scripts.
Requests
Yes, according to Matt, there are requests about it, on and off there are people in Bro mailing list asking about the availability of Bro signatures, so why not doing it to help the community?
I think these gives enough reasons for me to work on the project. But providing latest signatures is not the end of Emerging-Bro, I greatly appreciate the help from Seth Hall to step up and discuss with me about the direction of the project and we both agree that it should be the platform for people to share or contribute their policy/analysis scripts as well. Currently he has his own development repository here and I will import them to Emerging-Bro.
For the moment, you can access and download all the signatures at -
http://www.emergingthreats.net/bro/
Enough for now, and this project is also part of the reason why I'm not much blogging last two weeks as I have paid my free time to it. I would like to thank Matt and Seth for the collaboration works, and also Bro developers for their endorsement!
Cheers (;])
I'm now working closely with Matt Jonkman from EmergingThreats(ET) to start the new project calls Emerging-Bro, basically the project is about converting set of latest signatures from Snort to Bro so that Bro operators can take advantage of it. You can find more information from the announcement here -
http://www.emergingthreats.net/content/view/80/1/
If you are Bro operators, you might have question of why I'm doing this as Bro is more focused on policy and analysis script development to detect network event(be it normal or abnormal) instead of relying on signatures matching in byte stream. There are reasons why I'm doing this and I'm going to explain here -
Edge
Emerging-Bro will only focus on latest or critical signatures from ET, therefore the project is basically more concerning about latest/critical attacks because most networks are more vulnerable to newly discovered attacks than the old one, therefore detecting and preventing them at network boundary is much important. Currently there are about 100 latest signatures converted from ET to Emerging-Bro, and if you think certain Snort signature should be included, please do let me know.
Leverage
The signature set that is developed by EmergingThreats usually give little time window for attacker and reduce the outbreak period significantly, hence you can pretty quick in detecting initial stage of new attacks. Bro operators can take advantage of this if they can monitor the new attack in time and quickly develope more complete detection scheme with Bro policy scripts.
Requests
Yes, according to Matt, there are requests about it, on and off there are people in Bro mailing list asking about the availability of Bro signatures, so why not doing it to help the community?
I think these gives enough reasons for me to work on the project. But providing latest signatures is not the end of Emerging-Bro, I greatly appreciate the help from Seth Hall to step up and discuss with me about the direction of the project and we both agree that it should be the platform for people to share or contribute their policy/analysis scripts as well. Currently he has his own development repository here and I will import them to Emerging-Bro.
For the moment, you can access and download all the signatures at -
http://www.emergingthreats.net/bro/
Enough for now, and this project is also part of the reason why I'm not much blogging last two weeks as I have paid my free time to it. I would like to thank Matt and Seth for the collaboration works, and also Bro developers for their endorsement!
Cheers (;])
Wednesday, July 02, 2008
Davix: Review
From Davix's main site -
DAVIX, a live CD for data analysis and visualization, brings the most important free tools for data processing and visualization to your desk. There's no hassle with installing an operating system or struggle to build the necessary tools to get started with visualization. You can completely dedicate your time to data analysis.
The clause above is definitely right above Davix liveCD!!!!!
When people ask me which liveCD I use frequently, I always advocate these 3 -
1. HeX liveCD (Network Based Forensics)
2. BackTrack liveCD (Penetration Testing)
3. Helix liveCD (Digital Forensics)
I have mentioned many times that I prefer liveCD which focuses on specific domain very well, and Davix is really one of those. Undoubtedly I would love to include Davix to my CD folder.
Before I start anything serious, lets view the screenshot after startup from the liveCD -
DAVIX, a live CD for data analysis and visualization, brings the most important free tools for data processing and visualization to your desk. There's no hassle with installing an operating system or struggle to build the necessary tools to get started with visualization. You can completely dedicate your time to data analysis.
The clause above is definitely right above Davix liveCD!!!!!
When people ask me which liveCD I use frequently, I always advocate these 3 -
1. HeX liveCD (Network Based Forensics)
2. BackTrack liveCD (Penetration Testing)
3. Helix liveCD (Digital Forensics)
I have mentioned many times that I prefer liveCD which focuses on specific domain very well, and Davix is really one of those. Undoubtedly I would love to include Davix to my CD folder.
Before I start anything serious, lets view the screenshot after startup from the liveCD -

It's based on SLAX, and I guess most of people know how good SLAX is after trying out BackTrack, DAVIX takes advantage of SLAX modularity, stability and hardware supports, I have tested it with my own hardwares and it works pretty well.
If you are familiar with linux desktop solution, you will definitely recognize that it is using KDE from the screenshot. Though I'm not fan of KDE, but KDE is always simple and easy to use for general users. Many of system configuration can be done via gui so it saves a lot of hassle figuring how to get the system working for you.
On top of that, DAVIX offers very informative resources for users to have great kickstart in learning data capturing, processing and visualization by providing a set of firefox bookmark toolbars, you can easily access all the information requires to study the topic, this can reduce time in studying certain tools and learning visualization techniques, and it also saves you from googling hassle. I like the idea of toolbars organization in firefox.
On the other hand, DAVIX also comes with its own manual which is about 108 pages, you can access it via KDE menu -> DAVIX -> DAVIX Manual. If you are serious about learning data visualization with DAVIX, I suggest you to start with its manual instead of playing around with the desktop without knowing what to do. It contains the basic guide of how to use all the tools that are delivered in DAVIX, the best part is you can follow the manual and learn it practically with all the tools available in DAVIX.
There are 3 main categories listed in Kde menu, they are Capture, Process, and Visualize. The Capture contains tools for you to perform data logging, especially network data. The Process contains tools to perform data processing so that the output of data processed can be parsed by visualization tools. The Visualize mainly contains all the tools for you to visualize the data set by generating different kind of images, diagrams or graphs. As I have mentioned you can just learn all the tools shipped by DAVIX with the comprehensive manual itself.
So what are the tools shipped with DAVIX, there are way too many that I can cover here, however here are my favourites -
1. Rumint
2. Tnv
3. Afterglow
4. Inetvis
5. Etherape
6. Gnuplot
7. Rrdtools
8. Mrtg
9. Wireshark
This is more to preference thingy as I have used those tools previously and familiar with them, I will need to explore the potential of other tools which I never use before. If you want to learn how those tools work, you can actually refer to the DAVIX manual, and then refer to the data set example which you can properly find in /usr/local/share/*, different tools may support different kind of data formats so that may require some learning curves. But the real question lies in what kind of visualization techniques should be applied to the data set you have so that it makes most sense.
After talking about all the good things, I still think there are few things worth improved.
1. Log sample
As this is the liveCD for data analysis and visualization, except that it has the example data set in /usr/local/share/*, it should provide a set of sample logs(apache, postfix, exim, proftpd and etc). Then demonstrating how to format them to feed those visualization tools will be great.
2. Fat taskbar
You may notice in the screenshot that the taskbar is quite big(double taskbar), this is nothing wrong, but if I have to offer a liveCD for visualization purpose, I would prefer to have everything slicker to give bigger space to display the images that I have generated from the data.
3. Unified keyboard shortcut
This is just my idea, when I work with images, I always like to zoom in and out. Zooming in allows you to focus on detail, zooming out on the other hand can improve macro view to understand the ratio or distribution of data. I do know different tools have always defined different keyboard shortcut layout. If zoom(in/out) uses same set of shortcut key settings across all the tools in DAVIX, that would be really great. I'm glad DAVIX offers gqview as the main application to display images as that's my favorite one with its ease of use interface.
4. Installer
Currently it comes with BackTrack Installer which is quite experimental, it needs some works to get it installed, I have tested the installer and it works fine(if you know what you are doing), I'm looking forward for easy installer in future.
By the way, one might ask why should I use DAVIX, simple enough. Take the old cliche "A Picture Is Worth A Thousand Words". Using correct visualization techniques to process your thousand lines log files, to be honest you can do more with less, it saves your times and brain power to focus on something more important.
Guess I should end my review about DAVIX here, in case you are interested to try out DAVIX -
DAVIX is also part of Raffael's upcoming book Applied Security Visualization which will be published by Addision Wesley.
Currently, DAVIX is only available to beta testers. To participate in testing, please contact jan.monsch at iplosion.com
Thanks to DAVIX development team for allowing me to participate in beta testing, later is better than never. I do know developing a liveCD require hard works if you want to build a solid one, kudos!
Update Note:
DAVIX developer Jan. P. Monsch has informed me that he has actually making the taskbar more slicker now in new version of Davix, thanks for taking positively on my input.
Enjoy (;])
Tuesday, July 01, 2008
Snort 3.0 Beta
If you are interested to check out what's offered by latest Snort, now you have it. Kudos to snort development team!!!!!
http://www.snort.org/dl/snortsp/
I haven't tried that out personally yet, but you should!
Enjoy ;]
http://www.snort.org/dl/snortsp/
I haven't tried that out personally yet, but you should!
Enjoy ;]
Tuesday, June 24, 2008
Earthquake? or Storm .....
The terrible disaster .....


The beijing.exe is actually the storm variant, I thought they are making use of festivals only, it seems they don't even let any single chance going with the use of disaster(popularity counts), that's going too far from humanity.
If you run it, it's really disaster!
If you run it, it's really disaster!
Peace :[
Sunday, June 22, 2008
Friday, June 20, 2008
Good Read on Bro's Signature Engine
The ICIR blog is always informative, and I'm quite please with the latest post about Bro's Signature Engine.
I just learned few things that I don't know from the post, and it appears that Bro uses flex's regular expression syntax. It is important to understand which condition to use when writing the signature .
Otherwise, take the good read on Things To Keep In Mind When Writing Signatures, that section is particularly useful if you are interested to write Bro sigs.
Peace ;]
I just learned few things that I don't know from the post, and it appears that Bro uses flex's regular expression syntax. It is important to understand which condition to use when writing the signature .
Otherwise, take the good read on Things To Keep In Mind When Writing Signatures, that section is particularly useful if you are interested to write Bro sigs.
Peace ;]
Wednesday, June 18, 2008
Forensics Tools
I have to do some forensics work, and the tools below are very handy -
http://www.afflib.org/
http://www.pyflag.net/cgi-bin/moin.cgi
http://ftimes.sourceforge.net/FTimes/
http://p2pmarshal.atc-nycorp.com/
Cheers ;]
http://www.afflib.org/
http://www.pyflag.net/cgi-bin/moin.cgi
http://ftimes.sourceforge.net/FTimes/
http://p2pmarshal.atc-nycorp.com/
Cheers ;]
M$: Server Hardening & Auditing
Don't laugh, sometimes you have to deal with this whether you like it or not.
I'm looking for tools to perform M$ Windows Server Hardening & Auditing, I know Microsoft Baseline Security Analyzer and IIS Lockdown but are there other tools you use to assist you in Hardening & Auditing operation such as hardening regedit keys, auditing Active Directory and so forth.
If your job is managing M$ Server Farm, how do you perform your task to make sure all servers have same set of configuration and policy, and they are all monitored properly?
I would like to hear from you, and recommend me good tools and methods of doing these. There's no real secure OS, there's only capable or bullshit sysadmin!
Wake up sysadmin, system security is part of your job .....
I'm looking for tools to perform M$ Windows Server Hardening & Auditing, I know Microsoft Baseline Security Analyzer and IIS Lockdown but are there other tools you use to assist you in Hardening & Auditing operation such as hardening regedit keys, auditing Active Directory and so forth.
If your job is managing M$ Server Farm, how do you perform your task to make sure all servers have same set of configuration and policy, and they are all monitored properly?
I would like to hear from you, and recommend me good tools and methods of doing these. There's no real secure OS, there's only capable or bullshit sysadmin!
Wake up sysadmin, system security is part of your job .....
Enjoy ;]
Tuesday, June 17, 2008
HeX 021: Learning PCRE and its performance
PCRE stands for Perl Compatible Regular Expressions, it is mainly used for pattern matching. If you want to learn more about PCRE, take a good read of its manual -
shell>man pcre
shell>man pcrematching
shell>man pcrepartial
shell>man pcrepattern
shell>man pcreperform
So why do you need to learn regular expressions(regex), here's the answer -
http://geek00l.blogspot.com/2006/12/regex-magic-for-netsexcanalyst.html
Next look at the tool that comes with pcre - pcretest, as the name implies, you can use pcretest to test your regex. Lets go -
shell>man pcre
shell>man pcrematching
shell>man pcrepartial
shell>man pcrepattern
shell>man pcreperform
So why do you need to learn regular expressions(regex), here's the answer -
http://geek00l.blogspot.com/2006/12/regex-magic-for-netsexcanalyst.html
Next look at the tool that comes with pcre - pcretest, as the name implies, you can use pcretest to test your regex. Lets go -
shell>pcre --help
Usage: pcretest [options] [input file [output file]]
Input and output default to stdin and stdout.
This version of pcretest is not linked with readline().
Options:
-b show compiled code (bytecode)
-C show PCRE compile-time options and exit
-d debug: show compiled code and information (-b and -i)
-dfa force DFA matching for all subjects
-help show usage information
-i show information about compiled patterns
-m output memory used information
-o
-p use POSIX interface
-q quiet: do not output PCRE version number at start
-S
-s output store (memory) used information
-t time compilation and execution
-t
-tm time execution (matching) only
-tm
If you have already read the man pages above, you should be able to understand some of the options, I normally use the option -C to check the compiles-time option first -
shell>pcretest -C
PCRE version 7.7 2008-05-07
Compiled with
UTF-8 support
Unicode properties support
Newline sequence is LF
\R matches all Unicode newlines
Internal link size = 2
POSIX malloc threshold = 10
Default match limit = 10000000
Default recursion depth limit = 10000000
Match recursion uses stack
Other option I usually use is -t to test on the time compilation and execution of particular regex I write.
shell>pcretest -t
PCRE version 7.7 2008-05-07
re>
So you may see the prompt goes to interactive mode - re>, it is for you to define your regex, bear in mind that your regex must use forward slash as delimeter, for example -
re>/[a-z0-9]+/
This means your regex is [a-z0-9]+, once you enter you will see this -
Compile time 0.0028 milliseconds
data>
You may notice the compile time for this regex is 0.0028 milliseconds, now you try to put any data to see if they match the regex,
data>ABC
Once you hit the enter, you will see this -
Execute time 0.0008 milliseconds
No match
The execution time is 0.0008 milliseconds and there's no match, lets change the data -
data> abc
Execute time 0.0004 milliseconds
0: abc
We can now see the execution time is 0.0004 milliseconds and the data seems to match the regex.
You can also figure out multiple regex compile time on the fly by defining them in a file instead of using interactive mode. For example I write the lines below to a file - pcre-testing.txt
/\d{,10000}/
/([a-z0-9]+)?/i
Do remember that if you want to test multi regex at once, you have to split them with a blank line, you can't do like this and it will incur errors -
/\d{,10000}/
/([a-z0-9]+)?/i
Now we can run this -
shell>pcretest -t pcre-testing
PCRE version 7.7 2008-05-07
/\d{,10000}/
Compile time 0.0032 milliseconds
/([a-z0-9]+)?/i
Compile time 0.0054 milliseconds
There are other options that you may want to try out, but I think I have given you enough guide to carry on, you may be interested in reading some of my related posts here -
http://geek00l.blogspot.com/2007/11/regex-learning-tool-kregexpeditor.html
http://geek00l.blogspot.com/2007/07/visualregexp-nice-regex-learning-tool.html
I advocate pcretest because it comes with pcre and available in HeX, and you can evaluate the performance of the regex quickly.
shell>pcretest -C
PCRE version 7.7 2008-05-07
Compiled with
UTF-8 support
Unicode properties support
Newline sequence is LF
\R matches all Unicode newlines
Internal link size = 2
POSIX malloc threshold = 10
Default match limit = 10000000
Default recursion depth limit = 10000000
Match recursion uses stack
Other option I usually use is -t to test on the time compilation and execution of particular regex I write.
shell>pcretest -t
PCRE version 7.7 2008-05-07
re>
So you may see the prompt goes to interactive mode - re>, it is for you to define your regex, bear in mind that your regex must use forward slash as delimeter, for example -
re>/[a-z0-9]+/
This means your regex is [a-z0-9]+, once you enter you will see this -
Compile time 0.0028 milliseconds
data>
You may notice the compile time for this regex is 0.0028 milliseconds, now you try to put any data to see if they match the regex,
data>ABC
Once you hit the enter, you will see this -
Execute time 0.0008 milliseconds
No match
The execution time is 0.0008 milliseconds and there's no match, lets change the data -
data> abc
Execute time 0.0004 milliseconds
0: abc
We can now see the execution time is 0.0004 milliseconds and the data seems to match the regex.
You can also figure out multiple regex compile time on the fly by defining them in a file instead of using interactive mode. For example I write the lines below to a file - pcre-testing.txt
/\d{,10000}/
/([a-z0-9]+)?/i
Do remember that if you want to test multi regex at once, you have to split them with a blank line, you can't do like this and it will incur errors -
/\d{,10000}/
/([a-z0-9]+)?/i
Now we can run this -
shell>pcretest -t pcre-testing
PCRE version 7.7 2008-05-07
/\d{,10000}/
Compile time 0.0032 milliseconds
/([a-z0-9]+)?/i
Compile time 0.0054 milliseconds
There are other options that you may want to try out, but I think I have given you enough guide to carry on, you may be interested in reading some of my related posts here -
http://geek00l.blogspot.com/2007/11/regex-learning-tool-kregexpeditor.html
http://geek00l.blogspot.com/2007/07/visualregexp-nice-regex-learning-tool.html
I advocate pcretest because it comes with pcre and available in HeX, and you can evaluate the performance of the regex quickly.
Enjoy (;])
Wednesday, June 11, 2008
Monday, June 09, 2008
MSN IM -> Blogspot -> Pr0ning
I came across this seductive message, and it contains the link that I can't resist to click since it is asked by horny ladies, the link must be legitimate -
http://cux7850mdmk.blogspot.com
http://cux7850mdmk.blogspot.com

 Once you click on it, that blog will bring you to another site which is -
Once you click on it, that blog will bring you to another site which is -http://66.111.45.170/cams/1/
You can see below what is loaded when you go to the blog that is setup with malicious purpose -
 The cut-down zoom in version -
The cut-down zoom in version -META http-equiv="refresh" content="0;URL=http://66.111.45.170/cams/1/"
I manually check http://66.111.45.170/cams, and you might enjoy the screenshot -

Lets see what is in http://66.111.45.170/cams/1/, the content location is actually at -
http://66.111.45.170/cams/1/index.htm
And the index.htm contains -
Now you should be happy to land at this page, and lets register as a member.
http://66.111.45.170/cams/1/index.htm
And the index.htm contains -
meta http-equiv="refresh" content="0; URL=http://www.xxxblackbook.com/?s=register&r=lc129795"
Now you should be happy to land at this page, and lets register as a member.

It's rather easy to get someone to click on "look legitimate" link than from the email spam these days. We see the use of meta http-equiv="refresh", and you can find the information about it here -
http://www.html-reference.com/META_httpequiv_refresh.htm
During discussion at freenode #rawpacket, my friend scholar pointed me out related information here -
http://spamtrackers.eu/wiki/index.php?title=Blogspot
Enjoy ;]
Sunday, June 01, 2008
Network Flow: Uni-Directional VS Bi-Directional
If you are working on network flow research, you should have heard about Uni-Directional and Bi-Directional Network Flow. I will try to explain what are they here. Lets take the quick look of what network flow is first -
Network Flow is the sequence of packets or a packet that belonged to certain network session(conversation) between two end points but delimited by the setting of flow generation tool. To cut it short, it provides network traffic summarization by metering or accounting certain attributes in the network session.
The endpoints here are defined as below -
Layer 2 Endpoint - Source Mac Address | Destination Mac Address
Layer 3 Endpoint - Source IP Address | Destination IP Address
Layer 4 Endpoint - Source Port | Destination Port
Before we dive into understanding of UniFlow and BiFlow, lets look at the definition of Uni and Bi here -
http://www.yourdictionary.com/uni-prefix
http://www.yourdictionary.com/bi-prefix
Uni - one; having or consisting of one only; regarded as a single entity
Bi - using two or both; joining two, combining or involving two
In the context of Uni/Bi Directional Flow, Uni means single, Bi means both. Now, let make it more clearer.
Uni-Directional = Single Directional
Bi-Direction = Both Directional
I put up the illustration in the diagram below.
Uni-Directional Flow
Network Flow is the sequence of packets or a packet that belonged to certain network session(conversation) between two end points but delimited by the setting of flow generation tool. To cut it short, it provides network traffic summarization by metering or accounting certain attributes in the network session.
The endpoints here are defined as below -
Layer 2 Endpoint - Source Mac Address | Destination Mac Address
Layer 3 Endpoint - Source IP Address | Destination IP Address
Layer 4 Endpoint - Source Port | Destination Port
Before we dive into understanding of UniFlow and BiFlow, lets look at the definition of Uni and Bi here -
http://www.yourdictionary.com/uni-prefix
http://www.yourdictionary.com/bi-prefix
Uni - one; having or consisting of one only; regarded as a single entity
Bi - using two or both; joining two, combining or involving two
In the context of Uni/Bi Directional Flow, Uni means single, Bi means both. Now, let make it more clearer.
Uni-Directional = Single Directional
Bi-Direction = Both Directional
I put up the illustration in the diagram below.
Uni-Directional Flow


Bi-Directional Flow
 Now I will make a simple example, host A sends 90 bytes to host B and host B replies with 120 bytes. Here's the output -
Now I will make a simple example, host A sends 90 bytes to host B and host B replies with 120 bytes. Here's the output -Uni-Directional Network Flow
Srcaddr Direction Dstaddr Total Bytes
Host A -> Host B 90
Host B -> Host A 120
Bi-Directional Network Flow
Srcaddr Direction Dstaddr Total Bytes Src Bytes Dst Bytes
Host A <-> Host B 210 90 120
The Srcaddr and Dstaddr are the endpoints here. In Uni-Directional Flow, you only see the total bytes that sent by Host A(attribute of Host A) but nothing about Host B in the first flow record. Then the next record shows Host B sends 120 bytes to Host A(attribute of Host B). The total bytes is accounted from single endpoint(either Host A or B) only. But in BiFlow, you can see that Host A sends 90 bytes(Source Bytes) and Host B replies with 120 bytes(Destination Bytes). The total bytes is the accumulation of source and destination bytes. To summarize them -
Uni-Directional Network Flow Model - One direction at a time, every flow record contains the attribute of single endpoint only.
Bi-Directional Network Flow Model - Both direction at a time, every flow record contains the attribute of both endpoints.
Theory is tough sometime, here's the practical sample -
Cisco NetFlow uses Uni-Directional model for flow generation
Argus uses Bi-Directional model for flow generation
To draw good picture of Uni-Directional and Bi-Directional Network Flow, it's best to do comparison of them.
1. Network Flow data which is generated by Argus 3 natively
2. Network Flow data which is generated by Cisco NetFlow version 5
The flow records below are generated from the same network session. You can examine closely by clicking on them.
Cisco NetFlow(UniFlow):
Uni-Directional Network Flow Model - One direction at a time, every flow record contains the attribute of single endpoint only.
Bi-Directional Network Flow Model - Both direction at a time, every flow record contains the attribute of both endpoints.
Theory is tough sometime, here's the practical sample -
Cisco NetFlow uses Uni-Directional model for flow generation
Argus uses Bi-Directional model for flow generation
To draw good picture of Uni-Directional and Bi-Directional Network Flow, it's best to do comparison of them.
1. Network Flow data which is generated by Argus 3 natively
2. Network Flow data which is generated by Cisco NetFlow version 5
The flow records below are generated from the same network session. You can examine closely by clicking on them.
Cisco NetFlow(UniFlow):
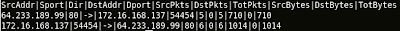
Argus(BiFlow):
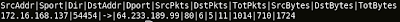
Flow record property:
SrcAddr = Source Address
Sport = Source Port
Dir = Direction
DstAddr = Destination Address
Dport = Destination Port
SrcPkts = Source Packets
DstPkets = Destination Packets
TotPkts = Total Packets
SrcBytes = Source Bytes
DstBytes = Destination Bytes
TotBytes = Total Bytes
Sometimes I like to think that UniFlow is stateless and BiFlow is stateful.
I will continue writing this Network Flow series, and I hope you enjoy it. Stay tuned for the next one - Traffic Matrix. And of course the HeX 021 series too.
Argus 3 Tip:
You can convert Argus BiFlow to UniFlow by using -M rmon option.
Peace (;])
Friday, May 30, 2008
Network Flow: TopN
There are a lot of questions popping up on and off in argus mailing list regarding how to generate TopN output from argus data, but frequently you may find the questions are too rough to give complete answer.
I'm going to discuss about TopN this time, TopN is the technique that widely used in many industries, what is it for?
TopN is used to retrieve the first N records from the data based on certain object and ordered by its property. Since I'm talking about Network Flow, I would like to make the example using it.
Data: Network Flow Record
Object: Protocol, Network, IP(host), Port, etc
Object Property: Packet Count, Byte Count, etc
Bear in mind that I'm avoiding the use of Flow terminology but layman one so that this example can be understood easily.
If you want to use TopN technique to generate information from the network flow data, first you need to know what you are looking for. Lets go with a simple one -
I want to find out Top 5 IP ordered by Total Packet Count
Total Packet Per IP(host) = (packet send + packet receive) Per IP(host)
Now you run the argus client command to parse the data and generate exactly the result which looks like this -
shell>racluster -M rmon -m saddr -nr testing.arg3 -w - | \
rasort -m pkts -w - | \
ra -L0 -N 5 -s saddr pkts
SrcAddr TotPkts
172.16.1.108 993
193.231.236.41 824
211.185.125.124 178
172.16.1.103 56
211.180.229.190 36
The command above is to generate Top 5 IP ordered by Packet Count. Don't ask me about the command line, it looks complicated for now but that's not my point here, look at the output instead. Host 172.16.1.108 sends or receives 993 pakcets, followed by 193.231.236.41 and so forth.
Now if you want to locate Top 5 IP ordered by Byte Count. You can just run -
shell>racluster -M rmon -m saddr -nr testing.arg3 -w - | \
rasort -m bytes -w - | \
ra -L0 -N 5 -s saddr bytes
SrcAddr TotBytes
172.16.1.108 599949
193.231.236.41 579050
211.185.125.124 18901
172.16.1.103 4964
216.168.224.69 3458
You want to use TopN, you should draft out the TopN output you are looking for, I have seen questions like this -
1. Which is the most active network?
2. Who is the most active sender?
3. Who is the most active receiver(got ddos?)
Or worse,
How can I find out the top talkers?
These kind of questions are too loose, you should at least specify the property, such as most active sender that is ordered by packet count, or most active network that is ordered by byte count and so forth. You have to bear in mind that packet and byte are not going inline, you can have one host sending many small size packets which won't hit TopN byte count at all.
With this kind of idea in mind, you can build the list of TopN which can draw you a good picture of network activeness to solve different issues.
For the next round, I will introduce Traffic Matrix, stay tuned!
Enjoy (;])
I'm going to discuss about TopN this time, TopN is the technique that widely used in many industries, what is it for?
TopN is used to retrieve the first N records from the data based on certain object and ordered by its property. Since I'm talking about Network Flow, I would like to make the example using it.
Data: Network Flow Record
Object: Protocol, Network, IP(host), Port, etc
Object Property: Packet Count, Byte Count, etc
Bear in mind that I'm avoiding the use of Flow terminology but layman one so that this example can be understood easily.
If you want to use TopN technique to generate information from the network flow data, first you need to know what you are looking for. Lets go with a simple one -
I want to find out Top 5 IP ordered by Total Packet Count
Total Packet Per IP(host) = (packet send + packet receive) Per IP(host)
Now you run the argus client command to parse the data and generate exactly the result which looks like this -
shell>racluster -M rmon -m saddr -nr testing.arg3 -w - | \
rasort -m pkts -w - | \
ra -L0 -N 5 -s saddr pkts
SrcAddr TotPkts
172.16.1.108 993
193.231.236.41 824
211.185.125.124 178
172.16.1.103 56
211.180.229.190 36
The command above is to generate Top 5 IP ordered by Packet Count. Don't ask me about the command line, it looks complicated for now but that's not my point here, look at the output instead. Host 172.16.1.108 sends or receives 993 pakcets, followed by 193.231.236.41 and so forth.
Now if you want to locate Top 5 IP ordered by Byte Count. You can just run -
shell>racluster -M rmon -m saddr -nr testing.arg3 -w - | \
rasort -m bytes -w - | \
ra -L0 -N 5 -s saddr bytes
SrcAddr TotBytes
172.16.1.108 599949
193.231.236.41 579050
211.185.125.124 18901
172.16.1.103 4964
216.168.224.69 3458
You want to use TopN, you should draft out the TopN output you are looking for, I have seen questions like this -
1. Which is the most active network?
2. Who is the most active sender?
3. Who is the most active receiver(got ddos?)
Or worse,
How can I find out the top talkers?
These kind of questions are too loose, you should at least specify the property, such as most active sender that is ordered by packet count, or most active network that is ordered by byte count and so forth. You have to bear in mind that packet and byte are not going inline, you can have one host sending many small size packets which won't hit TopN byte count at all.
With this kind of idea in mind, you can build the list of TopN which can draw you a good picture of network activeness to solve different issues.
For the next round, I will introduce Traffic Matrix, stay tuned!
Enjoy (;])
Thursday, May 29, 2008
Laptop: Alternatives For Security Road Warrior
Which laptop model are you using? This is my question today. I have been looking for laptop of choice for myself, as a security road warrior, I prefer it to be -
1. Lightweight(small/medium size and compact)
2. Black and solid look
3. Miminum 150G of Disk and 4G of Rams
4. Great keyboard touch build(old thinkpad?)
5. 12-14inch display
6. Good battery life
7. FreeBSD/Linux Compatible or I will use VMware/VirtualBox
Currently there are 3 laptop models I have in my mind -
1. Macbook Black
2. Thinkpad T61
3. Dell Xps m1330
What do you think and what's your favorite laptop if you work in security industry, and you need to travel frequently? I'm looking forward for any good suggestion and sharing. Thanks!
1. Lightweight(small/medium size and compact)
2. Black and solid look
3. Miminum 150G of Disk and 4G of Rams
4. Great keyboard touch build(old thinkpad?)
5. 12-14inch display
6. Good battery life
7. FreeBSD/Linux Compatible or I will use VMware/VirtualBox
Currently there are 3 laptop models I have in my mind -
1. Macbook Black
2. Thinkpad T61
3. Dell Xps m1330
What do you think and what's your favorite laptop if you work in security industry, and you need to travel frequently? I'm looking forward for any good suggestion and sharing. Thanks!
Peace ;]
Subscribe to:
Posts (Atom)














